Boosting SecOps effectiveness: Tackling OT training gaps
The vulnerability of industrial control systems (ICS) to cyber attacks has reached worrying levels.
The SANS Institute’s study, titled “Breaking IT/OT Silos With ICS/OT Visibility,” (July 2023), highlights a critical concern – the lack of visibility in operational technology (OT) assets.
More than half of the surveyed security leaders (54%) identified the main limitation for improving security operations (SecOps), as the insufficient OT training provided to IT staff.
Let’s take a closer look at the urgency of addressing this problem, recent research findings, and see how with taking proactive measures, organisations can fortify their ICS infrastructure and protect critical operations from devastating cyber attacks.
Within today’s digitalised landscape, ICS, which are a major subset within OT, have emerged as an attractive target for cyber criminals. The consequences of successful attacks on ICS can be severe, ranging from operational disruptions, to potential damage to public safety and the environment.
In May 2021, a ransomware attack was directed at Colonial Pipeline Inc., one of the largest fuel transportation systems in the United States. The effects were catastrophic, as the attack forced the facility into a complete shutdown for several days.
The aftermath?
An acute fuel shortage that sent prices skyrocketing, leaving consumers and businesses reeling.
In fact, more than 40% of global ICSs have been hit with malicious attacks during 2022.
Broadly speaking, as organisations increasingly integrate IT and OT systems, the connected interdependencies between these domains expose vulnerabilities that can be mercilessly exploited.
A recent report from Forescout Research has categorised the riskiest connected devices into four main category areas:
IT devices, such as laptops and smartphones;
IoT devices, like smart home appliances and wearable devices;
OT devices used in industrial control systems, such as power plants and manufacturing equipment;
and internet of medical things (IoMT) devices used in the healthcare sector, such as medical implants and patient monitoring systems.
The report data identifies the five riskiest device types within those four categories:
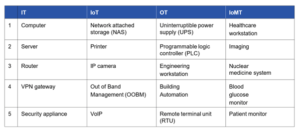
(*Table source: The Riskiest Connected Devices in 2023, Forescout Research.)
The report indicates that the risks associated with these devices, including weak security measures, outdated software, default or weak passwords, and lack of encryption.
The implications of the IT/OT divide
The knowledge divide between IT and OT poses serious risks to the security of industrial control systems. OT staff, responsible for the operation and maintenance of critical infrastructure, often lack the necessary understanding of modern cyber security threats. On the other hand, IT staff, with their expertise in cyber security, may struggle to comprehend the intricacies of OT systems. This knowledge gap leaves organisations vulnerable to attacks as threats increasingly target the convergence of IT and OT.
So what can organisations do?
Foster collaboration and knowledge sharing between IT and OT teams. Promote cross-training initiatives to bridge the gap in cyber security knowledge and understanding. This collaboration enhances the collective ability to recognise and respond to threats effectively.
Risk assessment
Begin by conducting a comprehensive risk assessment to identify potential vulnerabilities and prioritise mitigation efforts. Understand the specific threats and potential consequences to tailor security measures accordingly.
Regulation
Regulatory bodies and government agencies are increasingly recognising the urgency of securing ICS. They are implementing standards and regulations to ensure the implementation of robust cyber security measures. Compliance with these regulations not only helps protect critical infrastructure but also ensures public safety and trust in the overall security of these systems.
The security perspective
From a security standpoint, protecting ICS is a daunting task. ICS often rely on legacy technologies and were not originally designed with cyber security in mind. This poses unique challenges in terms of securing these systems against attack from sophisticated cyber threats.
Stay vigilant in applying software updates, security patches, and firmware upgrades to address known vulnerabilities promptly. Regularly assess the compatibility of legacy systems and explore modernisation options where necessary.
Linked with that.
Robust access controls
Implement stringent access controls, employing strong authentication mechanisms, privileged access management, and role-based access control (RBAC) to restrict unauthorised access to critical systems.
Recognising the critical need for improved visibility in OT assets and addressing the lack of training among IT and OT staff are crucial steps for organisations. By fostering collaboration and breaking down silos between these domains, we can strengthen our cyber security posture. Investing in comprehensive training programs and promoting effective communication will help proactively defend against cyber attacks, safeguard critical infrastructure, and protect public safety.
For more information
The team at CyberHive are at the forefront of quantum-safe cryptography and are developing products that address the challenges organisations face by the ever-increasing advances in cyber security threats.
Contact our specialist team at [email protected] to learn more.
Get in touch
If you have a question or would like some more information, contact us today.





